Start connecting your users to applications, not networks.
Core principles
Zero Trust Network Access (ZTNA) doesn’t require an IP address on the corporate network to access your private applications. Your users and applications will make outbound connections on demand while leveraging micro-tunnels and synthetic IPs that are not visible on the public Internet. All paths lead back to the Zero Trust Exchange, which will broker these connections on demand.
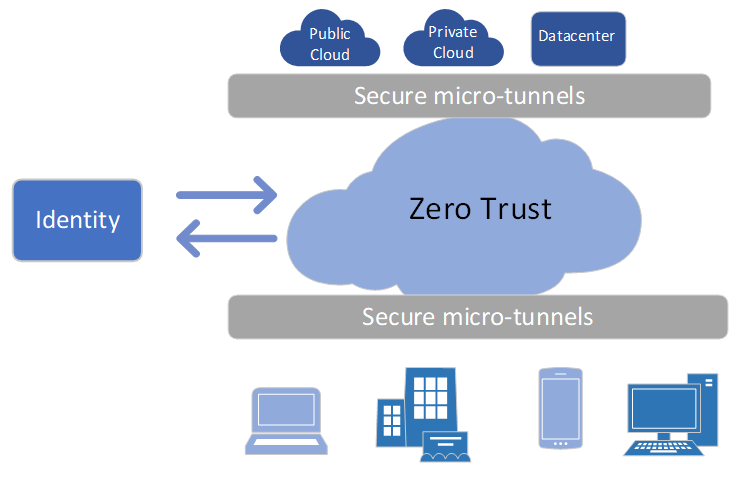
Applications are never exposed to the Internet. They are only visible to authenticated and legitimate end users. This model supports the new way of working – digital transformation.
Application segmentation is achieved on a per session per user basis on-demand. The underlying network simply becomes a transport to connect users to the desired applications, secured by utilizing micro-tunnels and TLS.
There is no VPN requirement for ZTNA. Instead, your end users will leverage secure TLS micro-tunnels in the outbound direction. There is no VPN appliance “listening” for inbound connections.
Rapid Adoption Factors
The traditional way of securing your corporate applications was to centralize them in datacenters and build out your perimeter security posture. Essentially creating a castle and moat architecture. You would then have to backhaul your users through your VPN appliances to securely connect them to your private applications and security stacks.
M&A Integration/Agility
Imagine that your company acquires another organization this quarter. You are tasked with integrating the new company with your corporate applications. In the past, you would have to connect the corporate networks together and hope that there is no IP overlap. Now you can combine corporate application access using multiple IdPs and granular security policies, while using the existing networks for transport only.
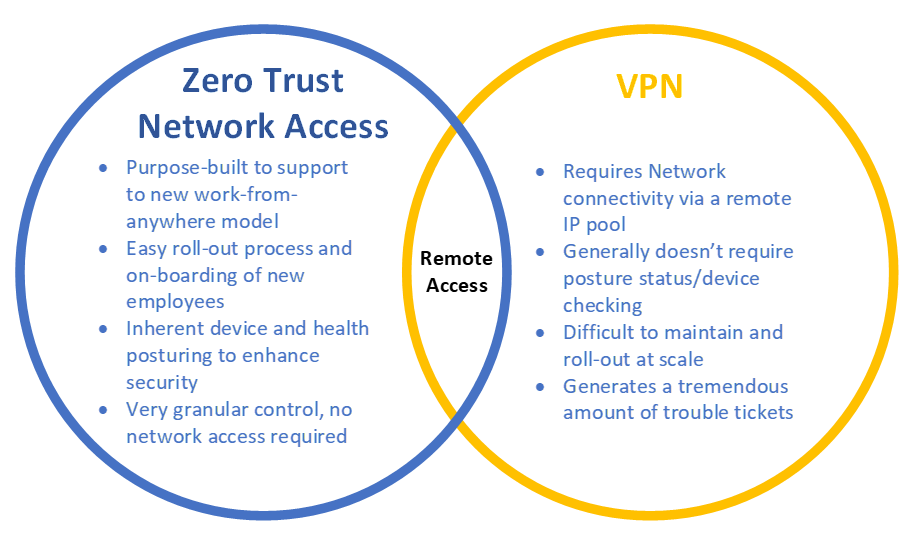
VPN Alternative
VPNs can become difficult to manage at scale and inherently introduce latency. As organizations begin to embrace the Work From Anywhere philosophy, ZTNA is the next evolution to support such a workforce. ZTNA leverages a distributed cloud architecture that will broker the user to applications, based on the closest available service edge.
Reduce Risk
Since your organization will no longer require your end users to obtain an IP address once connected to your VPN, you can significantly minimize risk. Users will gain access only to authorized applications, instead of the underlying corporate network. Lateral east-west movement on a network from a malicious attacker is significantly reduced.
Next Steps
If you’re interested in learning more about starting your journey toward an agile ZTNA network model, reach out to your WTG Account Executive today! WTG has partnered with leaders in this space and are uniquely positioned to help you say Goodbye to your VPN.


