Remote Access, Remote Connectivity, Teleworking, “Work from Home” – these are all terms that you are going to hear a lot during this unprecedented time in our workforce history. While the technologies that enable the remote workforce to exist have been around for a while, only now are we seeing this grow at an unprecedented rate. Unfortunately, this rapid transformation has left a big casualty in its wake… security. Now more than ever the bad actors of the world are attempting to find weaknesses in remote access solutions.
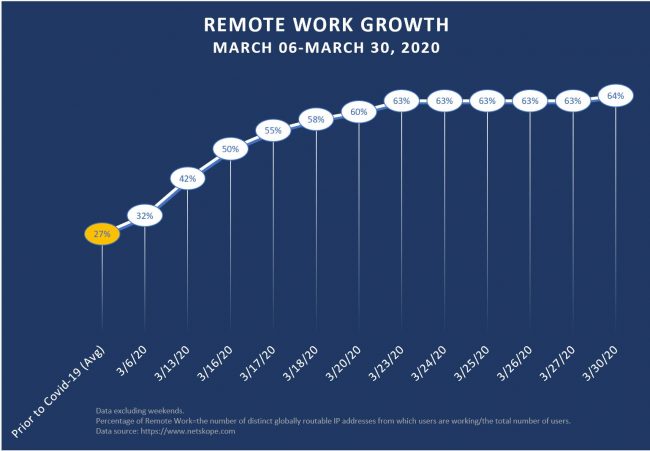
The chart below shows the increase in the remote workforce just over the month of March:
The graph shows an increase from an average of 27% prior to the pandemic to a staggering 64% of users working remotely (based on unique IP addresses). Now consider how much the threat landscape has also grown during this period – the following chart indicates how many new COVID-19 related domain names have been registered for the purpose of spreading malware:
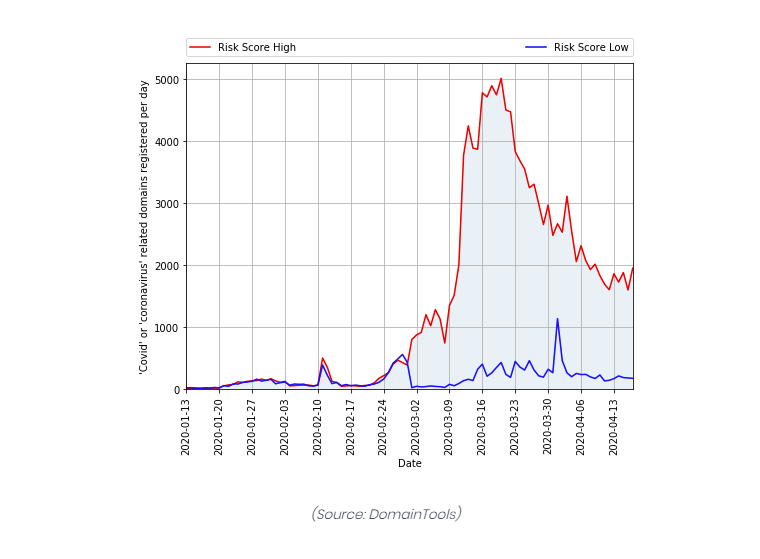
If you overlap these graphs, it paints a very scary picture! Now more than ever we must not think about security as an afterthought when implementing a remote access solution.
Many organizations have had some type of remote access over the years, whether it is via VPN or by another method such as a form of remote desktop/remote app (Citrix for example) or maybe a hardware appliance that you install at home (or your vacation home in Hawaii) that will give you access to company resources. There are also many organizations who are not utilizing remote access (at least at scale) and are now being forced to implement solutions that would typically take weeks of planning to just several days. This type of accelerated implementation can lead to quick decisions that could compromise security.
There are many ways to implement these types of connections – but what considerations should I think about before deploying one of these solutions?
There are a few things we need to look at as organizations to best decide on how we should give our employees remote access. Here are some considerations:
Username and password, please?
How will your users authenticate? One of the biggest risks that you can have on a remote access solution is weak username/password combinations (please do not use your birthday, house number or pet’s name). You should think about employing password requirements, i.e. minimum character length, complexity requirements, etc. If the solution can integrate with a directory service (such as AD) that is even better since you can centrally control password policies.
Consider Multi-factor Auth (MFA)
You should also think strongly about multi-factor authentication – if the solution supports it you should absolutely consider using it. There are many third-party products that can integrate with remote access solutions that can provide it as well. MFA can add that extra layer of security that helps fill the gaps with authentication weaknesses.
Are home devices safe to use to remotely access company resources?
The answer is yes and no. As an organization, you need to think about these devices as being outside of your control. This means you have limited access over what software may be installed, if the device is up on current patches, etc. If you do choose to allow employees to use home devices, there are some things you will want to do to ensure it’s done responsibly. If you are using VPN client software, ensure that your VPN networks are properly segmented in your firewall – think of how a DMZ works (where untrusted devices live), it’s the same type of consideration. If you use the “least privilege” methodology you can lock down client networks and minimize risk. Also, think about utilizing a remote access solution that Is “clientless” and would allow RDP sessions (to office workstations or “jump” servers) that could be accessed right through a browser – this would keep the traffic sufficiently “air-gapped”.
Think Long-Term
The on-going pandemic has certainly started a culture shift that many organizations never saw coming. Some that never thought a fully or mostly full remote workforce would ever work are now seeing the benefits of having employees work out of their homes. Over the past 20-25 years, the technology has finally matured enough to enable this climate shift. You should think long-term, when it is finally time for the employees and staff to return to work, how many may remain remote? How many will need more permanent remote access solutions? Does this put my organization more at risk?
The answer to that last question is simply – yes, you will increase risk. The good news is there are ways the risk can be minimized. With the proper controls and technology in place, you can ensure that your organization can remain protected from outside threats.
For Remote Workforce Assessment information, click here.