Defense-in-Depth. It’s time to revisit an old but tried and true model.
Here at WTG we’ve been spending a fair amount of time investigating the landscape that is cyber liability insurance, cyber litigation, breach, and loss. In looking at that landscape, we’ve been reminded of why our NIST CSF / Defense-in-Depth based approach to helping clients with risk is so important.
Defense-in-Depth (“DiD”) is simply a model that describes a layered approach to cybersecurity risk management. I’ve seen infographics that range from coffee filters to castles (complete with moat, of course) to onions to super boring “text art”. It says that we have layers of defense mechanisms to protect the organization, thus reducing risk. For example purposes, that protection could be a firewall, an MDR solution, a backup system, an insurance policy, or a compliance/framework security program.
DiD also tells us it is important to have overlap. For example, you may have a firewall that does anti-malware inspection. That doesn’t replace the need to have an endpoint anti-malware protection solution and strategy. If it gets past the firewall, the endpoint can catch it. When all that fails (and more) you have insurance as a last resort.
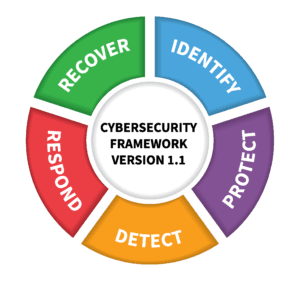 Consider DiD is not all about technical protection. In fact, in the NIST CSF (a simple DiD model shown at left) only one category really talks about technical protection (“protect”). The other categories or families or functions (“identify”, “detect”, “respond”, “recover”) are about process, data protection, risk assessment, operations, and so on.
Consider DiD is not all about technical protection. In fact, in the NIST CSF (a simple DiD model shown at left) only one category really talks about technical protection (“protect”). The other categories or families or functions (“identify”, “detect”, “respond”, “recover”) are about process, data protection, risk assessment, operations, and so on.
No service/solution/product/vendor/process/framework/policy can or will completely eliminate risk associated with cybersecurity. We can assess risk and use products and services to reduce risk, we can use frameworks to organize the approach, but we can never eliminate risk. You will always have an exposure. It could be a zero-day, could be a rogue employee, could be something we haven’t even contemplated yet.
Using the DiD approach within your organization includes protective technology. It also includes cyber liability insurance considerations, insider threats, incident response preparedness, recovery planning, and vulnerability identification. All with the goal of using layers to reduce risk to an acceptable level.
If you are interested in learning more about an effective Defense in Depth security strategy, please contact us.


