Dell OS10 Basics Part 2
Dell OS10 is Dell’s latest switch operating system. It is built on a Linux core and is Dell’s offering in the Open Networking space. It is NOT intended as an upgrade for switches running OS6 (N-Series) or OS9 (legacy S-Series), however, any Dell S- or Z-Series switch with a “-ON” in the name can run OS10. OS10 is licensed separately from the hardware because it can theoretically be run on any switch that supports the Open Network Install Environment (ONIE). As I am writing this, the current stable version of OS10 is v10.5.1.1, and it is available on a majority of Dell Datacenter switches including the 1G S3048-ON, the 10G S41xxx-ON line, the 25G and 100G S52xxF-ON line, and the 100G and 400G Z9xxxF-ON.
In this series of posts about OS10 switches, I hope to give you some knowledge about how OS10 works, and how to configure some of the basic functions within OS10. Feel free to contact us if you have further questions about OS10 switches and networking, or if you would like assistance with configuring your OS10 switches.
NOTE: This series will discuss OS10 Enterprise Edition which is licensed. There is also a no-cost Open Edition, which is just as powerful, but much more complicated to manage as it removes the switch-like command interface and requires you do everything with native Linux networking commands. For our purposes, OS10 refers to the Enterprise Edition, unless explicitly stated otherwise.
Before we dive into the details, please note that all account management within Dell OS10 is done from the configuration context (if you are not sure what that means, check out the first entry in this series).
The most common account management task is changing a password for an existing account. Unfortunately, because OS10 saves the password (after encrypting it) in the config, there is not a command that just changes the password. Before you can change the existing password, we need to see what the existing config for this user is. To check this, use the following show command from the execution context (or use the do form in another context):
show running-configuration users
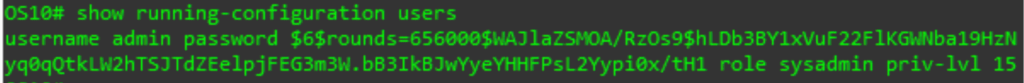
The thing we are checking here is the role sysadmin and priv-lvl 15 parts of the command. We want to duplicate these in the new command, so we do not inadvertently change the access level of the user when we change the password. With this data in hand, we can build the new command:
username XYZ password ABC role sysadmin priv-lvl 15
# XYZ is the username, ABC is the new password, and the role and priv-lvl are from the previous show command

The new password needs to meet the password complexity rules that are set on the switch. OS10’s maximum supported password length is 32 characters and in addition to upper and lowercase letters and numbers, it supports the following special characters: ! # % & ‘ ( ) ; < = > [ ] * + – . / : ^ _ The default minimum password length is 9 characters.
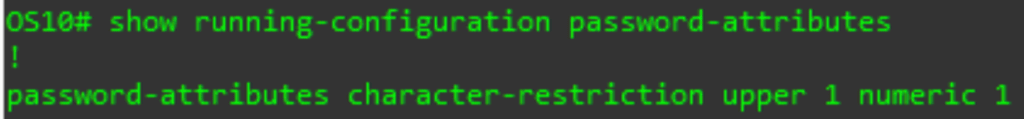
If you want to update the password complexity, you will use the password-attributes command. This command gives you a lot of options and flexibility, so I will not cover all of it. You can review the password-attributes section of the manual for all the gritty details. Here is one example, where we will require at least one upper case and one number.
password-attributes character-restriction upper X numeric Y
# X and Y can be any number from 0 to 31
![]()
You can also view the current complexity settings using the following show command:
Show running-configuration password-attributes
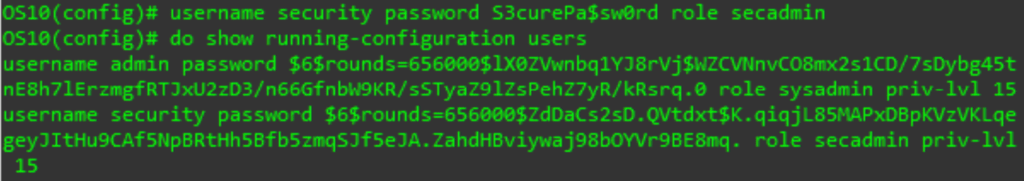
You can create a new user using the same command we used to change the password. Here is an excerpt from the manual detailing the different user roles. The priv-lvl is optional as the system will assign a default value based on the role.
- role role—Enter a user role:
- sysadmin — Full access to all commands in the system, exclusive access to commands that manipulate the file system, and access to the system shell. A system administrator can create user IDs and user roles.
- secadmin — Full access to configuration commands that set security policy and system access, such as password strength, AAA authorization, and cryptographic keys. A security administrator can display security information, such as cryptographic keys, login statistics, and log information.
- netadmin — Full access to configuration commands that manage traffic flowing through the switch, such as routes, interfaces, and ACLs. A network administrator cannot access configuration commands for security features or view security information.
- netoperator — Access to EXEC mode to view the current configuration. A network operator cannot modify any configuration setting on a switch.
- priv-lvl privilege-level — Enter a privilege level, from 0 to 15. If you do not specify the priv-lvl option, the system assigns privilege level 1 for the netoperator role and privilege level 15 for the sysadmin, secadmin, and netadmin
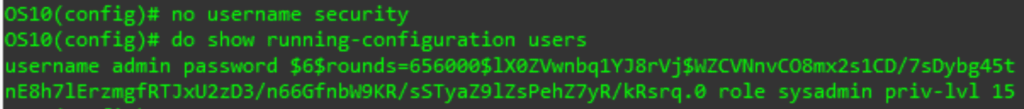
Lastly, you can remove a user using the no form of the username command:
no username XYZ
# XYZ is an existing username
There you have it. Now you should be able to create, view, update, and modify users on your OS10 switch. Maybe in a future article, we can discuss more advanced features like custom roles, or remote account management. For now, keep an eye out for the next entry in our OS10 series, looking at VLANs.
Click here for part 1!

